Reading Nutanix NCI 7.5 Through the Dark Site Upgrade Orchestrator
Why lifecycle enforcement becomes visible in air-gapped environments.
For a long time, dark sites were treated as a tolerated exception. Supported, but clearly outside the ideal operating path. If an environment had no internet access, the assumption was that operations would require more manual effort, more preparation, and a higher tolerance for risk.
With Nutanix Cloud Infrastructure 7.5, that assumption changes in a meaningful way. Dark sites are no longer treated as a secondary scenario. They are designed into the platform as a first class deployment model.
This is not a marketing shift. It is an architectural one.
In a previous article, I explored how Nutanix Infrastructure Manager reshapes the relationship between design and deployment. This piece continues that reading of NCI 7.5, focusing on lifecycle enforcement in isolated environments.
Offline does not mean unmanaged anymore
Historically, running a dark site implied a weaker lifecycle experience. Installation was possible, operations were supported, but upgrades were fragile, time consuming, and heavily dependent on manual preparation.
In NCI 7.5, isolated environments are expected to follow the same lifecycle principles as connected ones. Predictable, repeatable, and controlled.
The platform no longer assumes that connectivity is always available. Instead, it assumes that isolation might be intentional and permanent, and builds lifecycle workflows accordingly.
That single assumption changes everything.
Dark site upgrades as a design problem
The core challenge with dark site upgrades was never the lack of internet access. It was the lack of deterministic preparation.
Operators had to infer dependencies, collect artifacts manually, and validate compatibility indirectly. Success often depended more on experience and discipline than on tooling.
In NCI 7.5, upgrade preparation becomes explicit and enforced. Compatibility is calculated upfront. Required artifacts are clearly identified before execution. If something is missing, the process does not proceed.
This shifts upgrades from a best effort activity to a controlled operation. The difference is not speed. It is confidence.
Why predictability matters more in isolated environments
Dark sites usually exist for a reason. Regulatory requirements, security constraints, data sovereignty, or strict network isolation.
In these environments, downtime is expensive and experimentation is not an option. Lifecycle operations must be boring. Predictable always beats fast.
By treating dark sites as a first class scenario, Nutanix acknowledges that secure and isolated environments deserve the same operational maturity as connected ones. Isolation is no longer a justification for fragile processes.
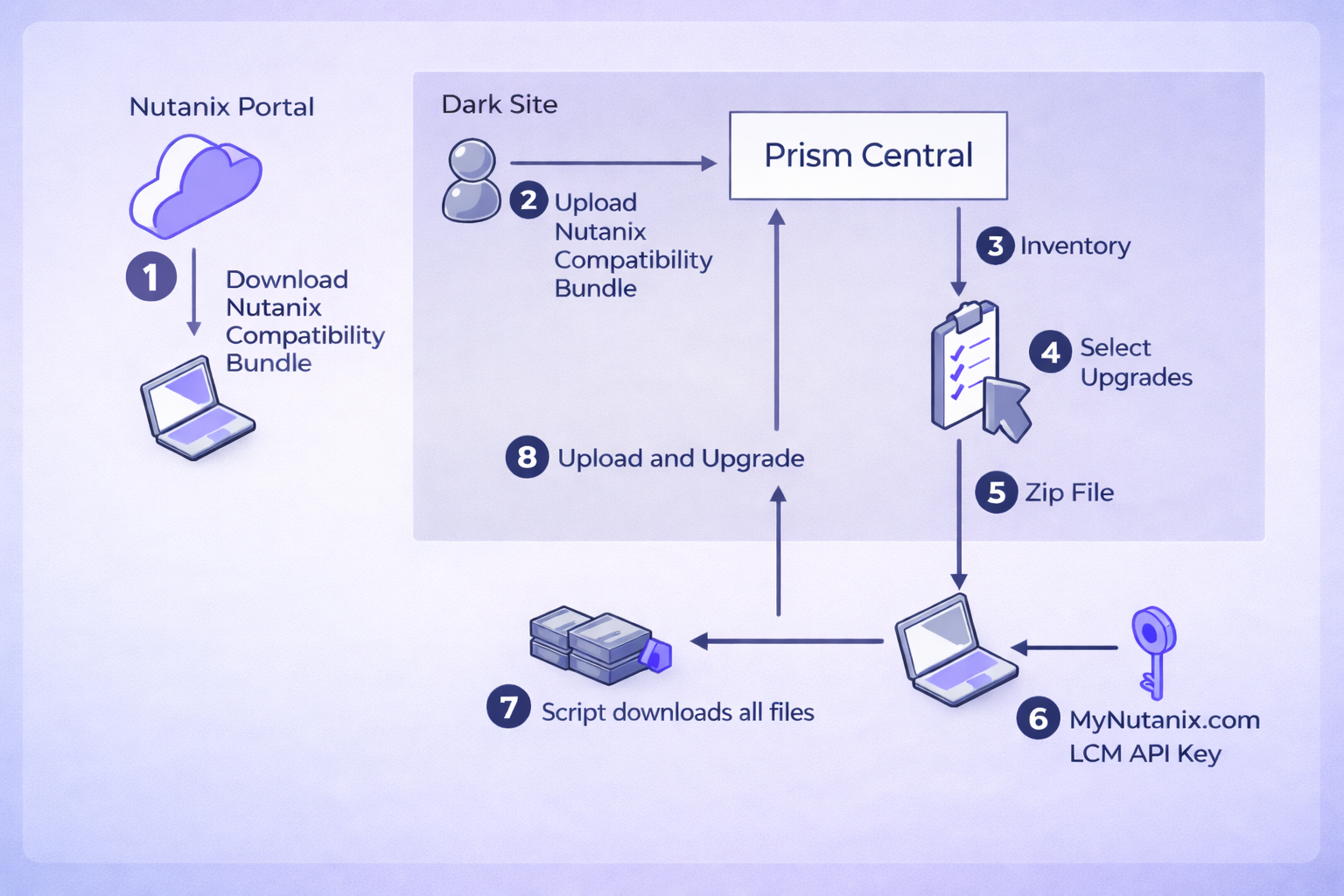
The dark site upgrade flow, simplified
The upgrade workflow used in dark site environments reflects this design philosophy.
Preparation and execution are intentionally separated. External systems are involved only where strictly required, while control, validation, and decision making remain inside Prism Central.
The initial interaction with the Nutanix portal is deliberately kept outside the dark site boundary. That step is limited to retrieving compatibility information and does not introduce any runtime dependency on external services.
Once that information is imported, the entire process is driven from within the isolated environment. Inventory analysis, upgrade selection, artifact validation, and execution remain under local control.
This structure is intentional. It allows air-gapped environments to follow the same operational logic as connected ones, without compromising security or predictability.
Dark sites and the broader enforcement model
Dark site improvements do not exist in isolation. They align with a broader shift visible across the platform.
Validated designs are enforced rather than documented. Network and security intent is applied rather than suggested. Lifecycle operations are guided rather than improvised.
Dark site lifecycle management follows the same pattern. Reduce reliance on human discipline. Increase reliance on platform enforcement.
When manual processes fail, they fail first in isolated environments. Designing for dark sites forces the platform to be explicit, opinionated, and consistent.
What does not disappear
Dark sites remain complex. That does not change.
They still require planning, staging, validation, and rollback strategies. Air-gapped environments do not become simple by default.
What changes is the relationship between the operator and the platform. The system no longer works against controlled environments. It supports a disciplined operating model instead of pushing complexity to the edges.
A quiet but important shift
There is nothing flashy about this change in NCI 7.5. And that is precisely the point.
When a platform stops treating isolation as an exception, it signals maturity. It shows that governance, lifecycle, and control matter more than constant connectivity.
For teams operating in regulated or secure environments, this is not a minor enhancement. It is the difference between tolerating a platform and trusting it.
Nutanix NCI 7.5 moves decisively in that direction.

